

Computer Security SeriesCleaning Infected Machines, Part 1
|
 |
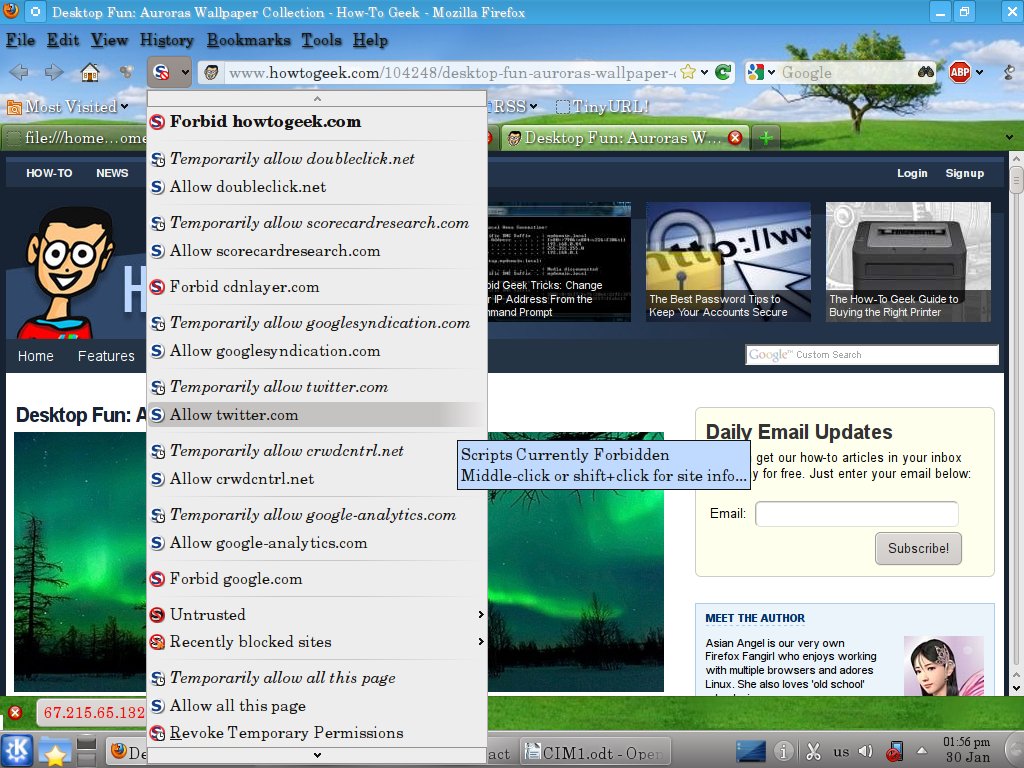
If NoScript has a flaw, it's you are going to whitelist potentially hundreds of sites. That gets old real fast. There is a work around though. If you go into the NoScript options, under General, check the “Temporarily allow top-level sites by default”, then chose “Base 2nd level domains”. While this does sacrifice a small amount of security, according to the NoScript site itself, “When a respectable site gets compromised, 99.9% of the times malicious scripts are still hosted on a different domain which is likely not in your whitelist, and gets just included by the pages you trust. Since NoScript blocks 3rd party scripts which have not been explicitly whitelisted themselves, you're still safe...” Beats turning NoScript off out of frustration by a long way.
Unfortunately for NoScript users, some sites, not a majority, but enough to be a nuisance, do use scripts that come from another domain. Symptoms that you need to whitelist a “3rd party” script include pictures not displaying, the site search box doesn't work, or clicking on links doesn't do anything. You will have to discover which domain(s) is the correct one to get full functionality from that website. However, once you white list these few, you'll be good to go. Since most people only regularly visit a few sites, it won't take long for you to build up a whitelist of your favorite sites that you trust or need to allow scripts to display, etc.
 |
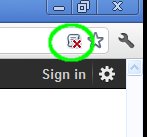
Chrome includes a similar function to NoScript, but no where near as powerful, nor as useful. You can tell Chrome to block all javascript by default, then selectively whitelist sites. To whitelist sites, click on the box with the red X through it in the upper right corner, then select “Always allow javascript on [site name]”. However, this allows all javascript on that page, even 3rd party scripts and you have to manually refresh the page to see the changes. Because so many sites effectively require javascript, and it doesn't block 3rd party scripts, it offers little protection.
 |
Internet Explorer (IE) users are out of luck for javascript protection. You can turn javascript off, on, or prompt. The prompt might sound like a reasonable compromise, but it prompts you on EVERY script on EVERY page. The prompt tells you nothing about the script wanting to execute, so can't selectively block. There is no whitelist feature. You won't last long before you just turn it back on. You can use the different zones to selectively allow javascript on some sites but not others, but then you run into the same problem as Chrome. Too many sites require javascript to function properly.
All modern versions of the browser mentioned, Chrome, Firefox, and Internet Explorer (version 8+) offer built in anti-phishing and anti-malware protection. Chrome and Firefox's are at least partially based off a Google list, while IE uses other source(s). Some researchers give IE the edge currently in blocking the bad sites. If your browser tells you it's a bad site, stay away!
Since XP SP2, every version of Windows comes with a free firewall. It's not the fanciest thing in the world, but it works, and should be enabled unless you have a very, very good reason to disable it. If you want to go with a fancier third party firewall, that's fine.
It seems strange that a simple, free with Windows, left with the default settings program can make a difference, but it can. A study by Craig Wright tested 640 XP SP2 machines. None had any antivirus, nor any users, and automatic updates were turned off (i.e. no patches). They were connected directly to the Internet and monitored to see how soon they were infected.
With Windows firewall turned off, the average time to infection was 18.16 hours. With Windows firewall turned ON, the average time to infection was 336 days, with the first infection happening in 108 days. Thus, the simple act of turning on the firewall made a significant difference.
Another simple step you can take to reduce the chances of getting infected is to not visit the websites that distribute malware and are involved in phishing. But how do you know which sites to avoid ahead of time, especially when the list changes constantly? You don't, but then, you don't have to.
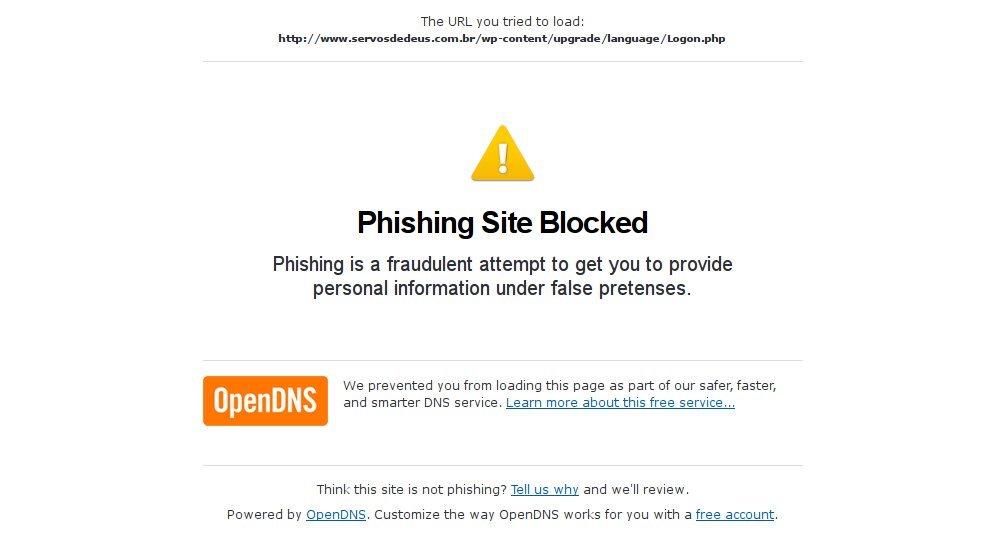
Several companies offer a free DNS filter service. These companies maintain realtime blacklists of malware, phishing, and spyware sites. By using their DNS servers, any attempt to reach the bad sites using a domain name will be blocked automatically. A simple, one-time change on your computer or home router can prevent an infection.
One of the biggest names that offers this service is OpenDNS, which also allows customized filters for a small fee. Simply change your DNS servers to 208.67.222.222 and 208.67.220.220 in your computer or router and you're done. HALNET members already have OpenDNS, so they don't have to do anything.
 |
There are a few others that also offer this service. Comodo offers their Comodo Secure DNS, and Symantec offers Norton DNS. Google's DNS service does not filter out malware and phishing sites and is not suitable for this purpose.
Be warned that, especially for people outside the United States, using these services may slow down your downloads and web surfing, despite their claims of speeding things up, so there is a trade-off.
Some readers might be thinking to themselves, “This is too much trouble. For starters, I don't know how to do some of things mentioned.” That's no excuse. There are computer user groups that can help you if you just ask, such as HAL-PC if you live in the Houston area. You could also pay someone to do it for you. Not doing these things pretty much guarantees you'll be paying someone to remove the malware later.
In addition to paying to remove the malware, you could be paying in other ways, quite literally. Ask Karen McCarthy, whose company lost $146,000 to malware and may go bankrupt, or Elie Kassab, who lost around $60,000, and the some 3,000 banks accounts in the UK drained of over $1 million.
There are tens of thousands more victims who's names never make the news. You can't afford not to take this seriously. Don't think your bank will protect you or reimburse you. Maybe they will, but you don't really want to take that chance. Karen McCarthy (above) found that out the hard way, as did Patco Construction, who lost $358,000 and the court battle to make the bank pay up.
Should you find out, or suspect your machine is infected, or one of your passwords is compromised, the clock is ticking. If it's a password compromised, and you can't find a good explanation, such as the website where you used that password was broken into, you should assume the worst. If you reused that password somewhere else, assume that account is compromised too. If it's not, it soon will be.
First, stop using the computer. Anything you do can be seen by the bad guys. This especially involves anything with usernames and passwords. Stored passwords and usernames can be harvested. It's probably too late, but an off computer can't transmit anything. An off computer also can't be destroyed. The Zeus trojan includes a kill operating system command which the criminals use as a diversion while they drain your accounts.
Second, using another, hopefully clean computer, or live CD, check any financial accounts you access from that computer. This includes, but is not limited to, credit cards, bank accounts, and brokerage accounts. If need be, stop in and see them or call them. If you call them, do not use the infected computer to look up the number. At least one trojan will throw up a fake support number if it detects you searching for one.
Next, check your backups (you do have backups right?) and get your computer cleaned. Just remember that your backups might have the malware included in the backup, and restoring from them could just reinstall the malware.
Finally, never reuse any of the old passwords. My experience at HALNET has taught me the criminals will try the old passwords again from time to time.
In part 2 of this series, I'll go over how to actually clean an infected computer, including a technique that some to many “professional” places don't use, but really should.
In addition to NoScript, there is another, confusingly similar, Firefox extension called RequestPolicy. The difference between the two is subtle. NoScript blocks javascript, Java, and Flash. It can do that whether they come from a third party site, or the site you are visiting itself. NoScript can not block http requests to another site, such as those found in many cross-site request forgery attacks.
RequestPolicy only blocks requests to another site. It can not block any content, such as malicious javascript or plugins coming from the site you are currently visiting. Only if the site calls them from another site, can RequestPolicy block them.
RequestPolicy suffers from the same problem as NoScript in that enough websites do use content from other domains legitimately that you have to go through the same whitelisting headaches. Further, RequestPolicy blocking can really mess up the way a page looks, much more than NoScript does. This is because sites do legitimately use content from third party sites, including content affecting the layout of the page, such as CSS files. When RequestPolicy is blocking content, a little flag in the lower right corner (visible in Figure 6) will be red. Click on that to see what's blocked an unblock it.
 |
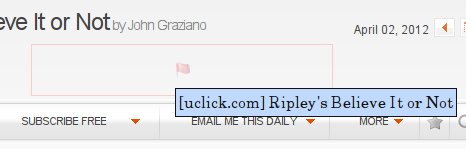 |
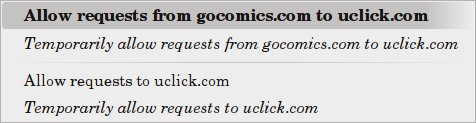
Some blocked content is displayed as a grayed out red flag as shown in Figure 7. If you hover over the flag, you'll see the site you need to unblock in order to see the content. You can then go down to the flag in the lower right corner and click on it (shown in Figure 6). Under blocked destinations will be, in this example, uclick.com. Hover the mouse pointer over that, and a new menu pops up, seen below. Click on the top choice to unblock permanently.
 |
You can run both NoScript and RequestPolicy at the same time. It which case, many legitimate cross-site requests must be whitelisted in both extensions. Between the two, NoScript is easier to use and will potentially impact your browsing less. But recognizing that desired content has been blocked is a bit harder and involves some trial and error on the unblocking.
If you are using NoScript as recommended in this article, RequestPolicy will give you better protection. RequestPolicy does make it easier to recognize content has been blocked and get it unblocked, often unblocking needed javascript as a side effect. But, you'll have to do it more often than with NoScript, and you'll be prompted on whenever a page tries to redirect you to another page. Usually, but not always, redirects are harmless and often helpful.
Chrome users have an extension called ScriptNo, which mimics many of NoScript's functions, although it is not affiliated with NoScript. It is recommend for Chrome users for the same reasons NoScript is recommended for Firefox users.
2012
Index
2011
July
June
April
March
February
January
2010
December
November
October
July
June
May
March
February
January
2009
Nov/Dec
October
September
August
July
June
May
April
March
February
January
2008
November/December
July
June
May
April
March
February
January
2007
November/December
October
September
August
July
June
May
April
March
February
January
2006
November/December
October
September
August
July
June
May
April
March
February
January
2005
Nov/Dec
October
September
August
July
June
May
April
March
February
January
2004
December
November
October
September
August
July
June
May
April
March
February
January